Introduction & Overview
Quantum computing represents a paradigm shift in computational power, leveraging principles of quantum mechanics to solve complex problems beyond the reach of classical computers. In the context of DevSecOps, quantum computing introduces transformative potential for security, optimization, and automation. This tutorial explores how quantum computing integrates into DevSecOps, offering a detailed guide for technical practitioners.
What is Quantum Computing?
Quantum computing uses quantum bits (qubits) that, unlike classical bits, can exist in multiple states simultaneously due to superposition and entanglement. This enables quantum computers to perform certain computations exponentially faster for specific problems, such as cryptography, optimization, and machine learning.
:max_bytes(150000):strip_icc()/quantum-computing-the-qbit-5c8aac5e46e0fb00016ee04e.jpg)
History or Background
- 1980s: Physicist Richard Feynman proposed quantum computers to simulate quantum systems.
- 1994: Peter Shor developed Shor’s algorithm, demonstrating quantum computers’ potential to break RSA encryption.
- 2019–2023: Companies like IBM, Google, and D-Wave released quantum hardware, achieving milestones like quantum supremacy.
- 2025 Context: Quantum computing is still nascent but increasingly accessible via cloud platforms like IBM Quantum and AWS Braket, impacting DevSecOps.
Why is it Relevant in DevSecOps?
Quantum computing is relevant to DevSecOps because:
- Security: Quantum algorithms threaten current cryptographic systems, necessitating quantum-resistant solutions.
- Optimization: Quantum algorithms can enhance CI/CD pipeline efficiency and vulnerability scanning.
- Scalability: Quantum-enhanced machine learning improves threat detection in real-time.
- Future-Proofing: DevSecOps teams must prepare for a post-quantum world, integrating quantum-safe practices.
Core Concepts & Terminology
Key Terms and Definitions
- Qubit: The basic unit of quantum information, capable of being in a superposition of 0 and 1.
- Superposition: A qubit’s ability to exist in multiple states simultaneously, enabling parallel computation.
- Entanglement: A quantum phenomenon where qubits become interconnected, allowing coordinated computations.
- Quantum Gate: Operations that manipulate qubits, analogous to logic gates in classical computing.
- Quantum Algorithm: Algorithms like Shor’s or Grover’s that leverage quantum mechanics for specific tasks.
- Post-Quantum Cryptography: Encryption methods resistant to quantum attacks, e.g., lattice-based cryptography.
| Term | Definition |
|---|---|
| Qubit | Quantum bit, the fundamental unit of quantum information. |
| Superposition | A state where a qubit can be in multiple states simultaneously. |
| Entanglement | A quantum state where qubits are linked and one qubit’s state depends on another. |
| Quantum Supremacy | The point at which a quantum computer can solve a problem that a classical computer practically cannot. |
| Quantum Gate | Basic building blocks of quantum circuits, similar to classical logic gates. |
| Quantum Circuit | A sequence of quantum gates applied to qubits. |
| Post-quantum cryptography (PQC) | Cryptographic algorithms designed to be secure against quantum attacks. |
How it Fits into the DevSecOps Lifecycle
Quantum computing impacts DevSecOps across:
- Plan: Designing quantum-safe architectures and threat models.
- Code: Developing quantum-resistant algorithms and libraries.
- Build: Testing quantum algorithms in CI/CD pipelines using quantum simulators.
- Test: Simulating quantum-based attacks to validate security.
- Release/Deploy: Integrating quantum-safe encryption in cloud deployments.
- Monitor: Using quantum-enhanced AI for real-time threat detection.
| DevSecOps Phase | Quantum Computing Relevance |
|---|---|
| Plan | Quantum threat modeling, secure architecture planning |
| Develop | Integration of PQC libraries |
| Build | Static checks against quantum vulnerabilities |
| Test | Simulation of quantum-safe cryptographic performance |
| Release/Deploy | Secure rollout using quantum-resistant keys |
| Monitor | Quantum-enhanced anomaly detection algorithms |
| Respond | Simulation of response strategies using quantum ML |
Architecture & How It Works
Components and Internal Workflow
Quantum computing systems in DevSecOps typically involve:
- Quantum Hardware: Qubits hosted on physical quantum computers (e.g., IBM’s superconducting qubits).
- Quantum Software: Frameworks like Qiskit or Cirq for programming quantum algorithms.
- Classical Integration: Hybrid systems combining classical and quantum computing via APIs.
- Cloud Access: Platforms like AWS Braket or Azure Quantum for remote quantum processing.
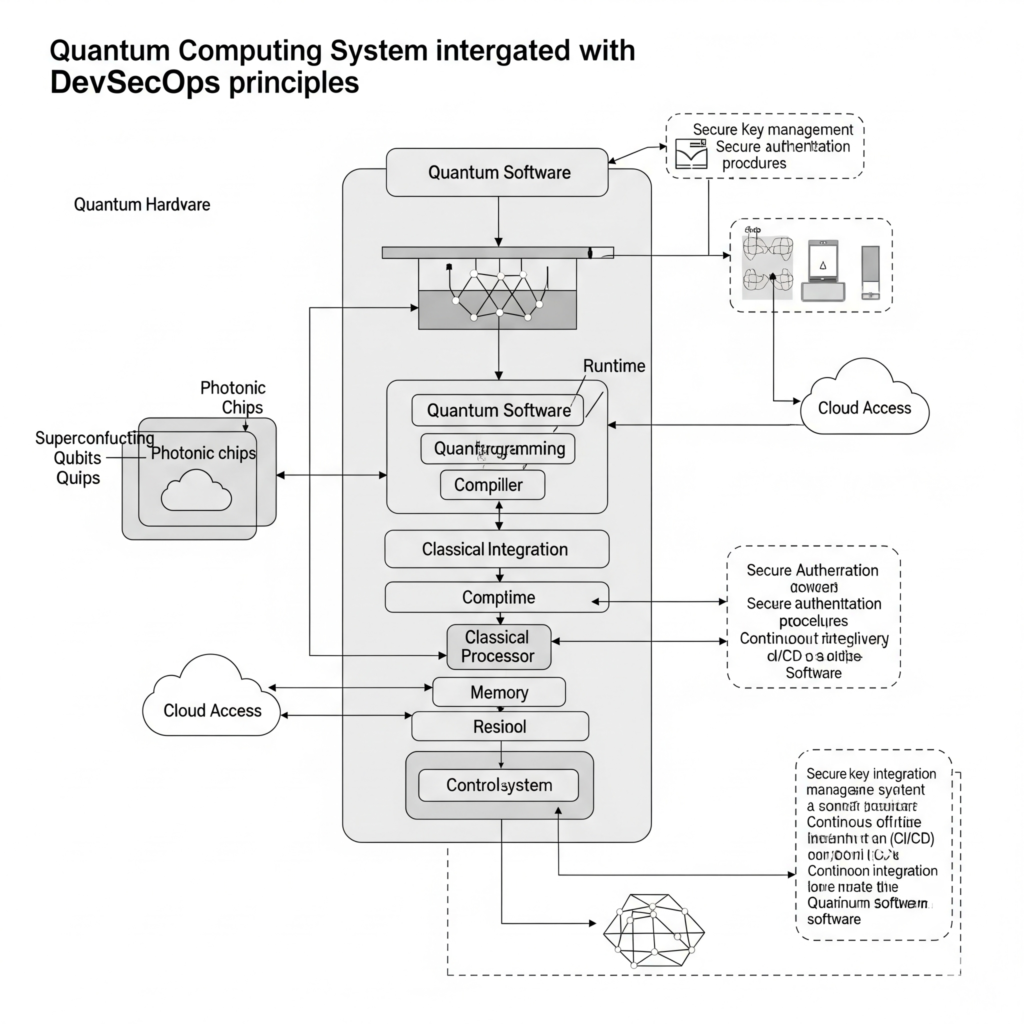
Workflow:
- A DevSecOps task (e.g., cryptographic analysis) is identified.
- Classical systems preprocess data and send specific computations to a quantum processor.
- Quantum algorithms process the data using qubits and gates.
- Results are returned to classical systems for post-processing and integration into CI/CD pipelines.
Architecture Diagram Description
Imagine a layered architecture:
- Top Layer (DevSecOps Tools): Jenkins, GitLab, or Kubernetes for CI/CD.
- Middle Layer (Quantum APIs): Interfaces like Qiskit or AWS Braket SDK to access quantum hardware.
- Bottom Layer (Quantum Hardware): Physical quantum processors or simulators hosted in the cloud.
- Data Flow: CI/CD pipelines send tasks to quantum APIs, which process them on quantum hardware and return results.
DevSecOps Pipeline
└── Pre-Commit Stage
└── Quantum Threat Detection Scripts (Cirq/Qiskit)
└── CI/CD Integration Layer
└── Hybrid Classical + Quantum API Layer
└── Quantum Cloud Provider
├── Quantum Simulator (Fallback)
└── Quantum Hardware (QPU)
Integration Points with CI/CD or Cloud Tools
- Jenkins/GitLab: Plugins to trigger quantum jobs (e.g., Qiskit for quantum circuit execution).
- Kubernetes: Orchestrating hybrid quantum-classical workloads via cloud quantum services.
- AWS Braket/Azure Quantum: Provide APIs to integrate quantum tasks into DevSecOps workflows.
Installation & Getting Started
Basic Setup or Prerequisites
- Hardware: A classical computer with internet access (quantum hardware is cloud-based).
- Software:
- Python 3.8+ for quantum frameworks like Qiskit.
- Cloud accounts for AWS Braket, IBM Quantum, or Azure Quantum.
- Docker for running quantum simulators locally (optional).
- Knowledge: Basic understanding of Python, DevSecOps pipelines, and quantum computing concepts.
Hands-on: Step-by-Step Beginner-Friendly Setup Guide
This guide sets up Qiskit with IBM Quantum for a simple quantum circuit in a DevSecOps pipeline.
- Install Python and Qiskit:
pip install qiskit qiskit-ibmq-provider- Set Up IBM Quantum Account:
- Sign up at https://quantum-computing.ibm.com/.
- Obtain an API token from the IBM Quantum dashboard.
3. Configure Qiskit with IBM Quantum:
from qiskit import IBMQ
IBMQ.save_account('YOUR_API_TOKEN')
IBMQ.load_account()- Create a Simple Quantum Circuit:
from qiskit import QuantumCircuit
# Create a quantum circuit with 2 qubits
circuit = QuantumCircuit(2, 2)
circuit.h(0) # Apply Hadamard gate
circuit.cx(0, 1) # Apply CNOT gate
circuit.measure([0, 1], [0, 1]) # Measure qubits- Integrate into CI/CD (e.g., GitLab CI):
Create a.gitlab-ci.ymlfile to run the quantum circuit:
stages:
- test
quantum_job:
stage: test
image: python:3.9
script:
- pip install qiskit qiskit-ibmq-provider
- python quantum_script.py- Run on IBM Quantum Simulator:
from qiskit import execute, Aer
simulator = Aer.get_backend('qasm_simulator')
job = execute(circuit, simulator, shots=1000)
result = job.result()
print(result.get_counts())- Test in Pipeline:
Push the code to GitLab, and the pipeline will execute the quantum circuit, simulating quantum computation.
Real-World Use Cases
1. Cryptographic Analysis
- Scenario: A DevSecOps team tests RSA encryption vulnerabilities using Shor’s algorithm.
- Implementation: Quantum circuits simulate factoring large numbers, identifying weaknesses in current encryption.
- Industry: Finance, where secure transactions are critical.
2. Optimization of CI/CD Pipelines
- Scenario: Optimize resource allocation in Kubernetes clusters using quantum annealing.
- Implementation: D-Wave’s quantum annealer solves scheduling problems faster than classical methods.
- Industry: Cloud providers like AWS or Google Cloud.
3. Threat Detection with Quantum Machine Learning
- Scenario: Enhance intrusion detection systems with quantum-enhanced AI.
- Implementation: Quantum support vector machines (QSVMs) analyze network traffic for anomalies.
- Industry: Cybersecurity firms.
4. Post-Quantum Cryptography Integration
- Scenario: Transition CI/CD pipelines to quantum-resistant algorithms like lattice-based cryptography.
- Implementation: Integrate NIST-approved post-quantum algorithms into DevSecOps workflows.
- Industry: Government and defense.
Benefits & Limitations
Key Advantages
- Speed: Solves specific problems (e.g., factorization, optimization) exponentially faster.
- Security: Enables testing of quantum-resistant algorithms.
- Scalability: Enhances AI-driven security tools in DevSecOps.
Common Challenges or Limitations
- Hardware Limitations: Current quantum computers have limited qubits and high error rates.
- Complexity: Requires expertise in quantum programming and DevSecOps integration.
- Cost: Access to quantum hardware via cloud services can be expensive.
- Maturity: Quantum computing is not yet fully mature for widespread DevSecOps adoption.
Best Practices & Recommendations
Security Tips
- Adopt NIST post-quantum cryptographic standards (e.g., CRYSTALS-Kyber).
- Regularly test quantum vulnerabilities in CI/CD pipelines.
- Use hybrid classical-quantum workflows to balance reliability and innovation.
Performance
- Use quantum simulators for testing to reduce costs before running on real quantum hardware.
- Optimize quantum circuits to minimize gate operations and errors.
Maintenance
- Monitor updates from quantum providers (e.g., IBM, AWS) for improved hardware and APIs.
- Maintain documentation of quantum workflows in DevSecOps pipelines.
Compliance Alignment
- Align with standards like NIST 800-53 for quantum-safe cryptography.
- Ensure quantum integrations comply with GDPR, HIPAA, or industry-specific regulations.
Automation Ideas
- Automate quantum circuit testing in CI/CD using tools like Jenkins or GitLab CI.
- Use Infrastructure as Code (IaC) to provision quantum resources via Terraform or AWS CDK.
Comparison with Alternatives
| Feature | Quantum Computing | Classical Computing | Hybrid Quantum-Classical |
|---|---|---|---|
| Speed for Cryptography | Exponential for specific tasks | Linear for most tasks | Balances speed and reliability |
| Security | Enables quantum-resistant crypto | Vulnerable to quantum attacks | Transitionary solution |
| Maturity | Emerging, limited hardware | Mature, widely available | Growing adoption |
| Cost | High (cloud-based access) | Low to moderate | Moderate |
When to Choose Quantum Computing
- Choose Quantum: For cryptography analysis, optimization problems, or quantum-safe algorithm development.
- Choose Alternatives: For general-purpose computing, cost-sensitive projects, or when quantum expertise is limited.
Conclusion
Quantum computing is poised to revolutionize DevSecOps by enhancing security, optimizing workflows, and preparing teams for a post-quantum future. While challenges like hardware limitations and complexity persist, early adoption through cloud platforms and simulators allows DevSecOps practitioners to stay ahead. Future trends include increased qubit counts, better error correction, and broader integration with CI/CD tools.
Next Steps
- Experiment with Qiskit or AWS Braket for hands-on quantum experience.
- Explore NIST’s post-quantum cryptography standards.
- Join quantum computing communities for collaboration.
Resources
- IBM Quantum Documentation: https://quantum-computing.ibm.com/
- AWS Braket Documentation: https://aws.amazon.com/braket/
- Qiskit Community: https://qiskit.org/community
- NIST Post-Quantum Cryptography: https://csrc.nist.gov/projects/post-quantum-cryptography