Introduction & Overview
What is a Quantum Execution Environment?
A Quantum Execution Environment (QEE) is a specialized runtime or platform that leverages quantum computing principles to execute software workloads, particularly for tasks requiring advanced cryptographic operations, optimization, or secure data processing. In DevSecOps, QEE integrates quantum-based processing into the software development lifecycle (SDLC) to enhance security, performance, and scalability while aligning with continuous integration, delivery, and security practices.
History or Background
Quantum computing originated in the 1980s with theoretical work by physicists like Richard Feynman and David Deutsch. By the 2020s, companies such as IBM, Google, and D-Wave advanced quantum hardware and software, making quantum applications feasible. The concept of QEE emerges as organizations explore quantum advantages in cryptography, machine learning, and secure multi-party computation, which are critical for DevSecOps. While traditional execution environments like containers and virtual machines dominate, QEE represents a next-generation approach for quantum-safe and optimized workloads.
Why is it Relevant in DevSecOps?
DevSecOps integrates security into every SDLC phase, emphasizing automation, collaboration, and rapid delivery. QEE is relevant because:
- Enhanced Security: Quantum algorithms (e.g., Shor’s for factoring, Grover’s for search) can strengthen or challenge cryptographic methods, necessitating quantum-resistant practices.
- Optimization: Quantum computing optimizes complex CI/CD tasks, such as vulnerability scanning or dependency analysis.
- Future-Proofing: QEE prepares organizations for quantum-safe pipelines and compliance with emerging standards like NIST post-quantum cryptography.
Core Concepts & Terminology
Key Terms and Definitions
- Quantum Execution Environment (QEE): A runtime platform using quantum or quantum-inspired resources to execute workloads, often in hybrid quantum-classical setups.
- Quantum Circuit: A sequence of quantum gates applied to qubits for computations, such as cryptographic key generation.
- Qubit: The basic unit of quantum information, enabling parallel computation via superposition and entanglement.
- Shift-Left Security: Integrating security early in the SDLC, enhanced by QEE’s rapid cryptographic checks.
- Hybrid Quantum-Classical Pipeline: A CI/CD pipeline combining quantum and classical computing for tasks like secure code signing.
| Term | Definition |
|---|---|
| QEE | A sandboxed runtime for executing quantum jobs. |
| Quantum Circuit | A series of quantum logic gates acting on qubits. |
| Hybrid Job | Workloads involving both classical and quantum compute. |
| QPU | Quantum Processing Unit – the actual quantum hardware. |
| Simulator | Classical emulation of quantum computation. |
| Post-Quantum Cryptography (PQC) | Algorithms resistant to quantum attacks. |
How It Fits into the DevSecOps Lifecycle
QEE integrates across the DevSecOps lifecycle:
- Plan: Quantum algorithms for threat modeling to identify vulnerabilities in code or architecture.
- Code: Quantum-safe cryptographic libraries to secure code commits.
- Build: Optimizing dependency resolution or static analysis with quantum algorithms.
- Test: Quantum-enhanced security tests (e.g., quantum fuzzing for vulnerability detection).
- Deploy: Securing deployment configurations with quantum key distribution (QKD).
- Monitor: Quantum machine learning for anomaly detection in production.
| DevSecOps Phase | QEE Role |
|---|---|
| Plan | Model secure quantum-enhanced use cases. |
| Develop | Code quantum circuits using SDKs (Qiskit, Q#, etc.) |
| Build | Compile hybrid jobs in containers using QEE buildpacks. |
| Test | Run unit/integration tests on simulators/QPU. |
| Release | Securely deploy via QEE-integrated pipelines. |
| Operate | Monitor and audit QPU access, resource usage. |
| Protect | Enforce PQC and zero-trust for quantum workloads. |
Architecture & How It Works
Components
- Quantum Runtime: Executes quantum circuits, provided by platforms like IBM Quantum or Qiskit Runtime.
- Classical Interface: APIs or SDKs (e.g., Qiskit, Cirq) to integrate quantum tasks with classical CI/CD tools.
- Security Layer: Quantum-safe cryptographic libraries (e.g., OpenQuantumSafe) for encryption and authentication.
- Orchestration Layer: Manages hybrid quantum-classical workloads, integrating with tools like Jenkins or GitLab.
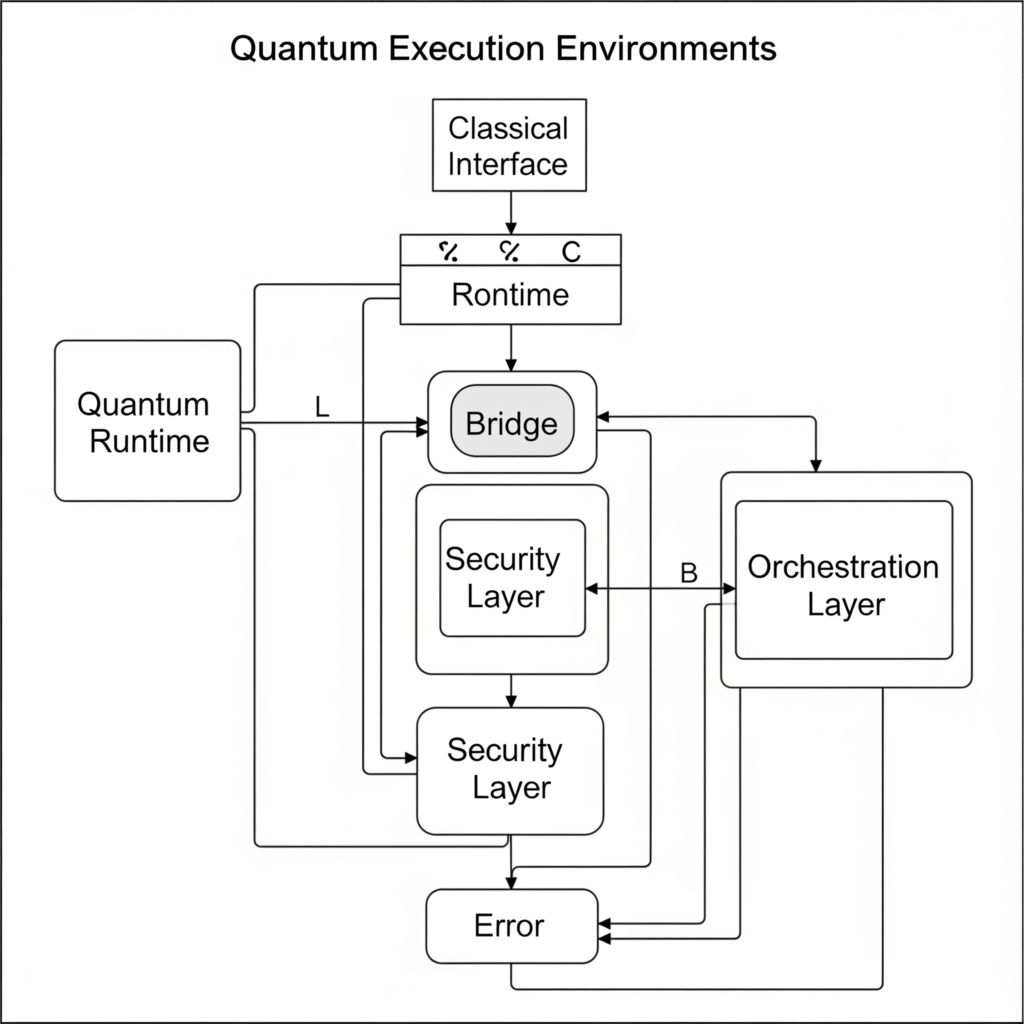
Internal Workflow
- Input Processing: The classical CI/CD pipeline sends tasks (e.g., cryptographic key generation) to the QEE.
- Quantum Computation: QEE executes quantum circuits on a quantum processor or simulator.
- Result Integration: Outputs (e.g., secure keys, optimized configurations) are returned to the classical pipeline.
- Security Validation: Quantum-safe checks ensure compliance with standards like NIST post-quantum cryptography.
Architecture Diagram (Description)
The architecture includes:
- CI/CD Pipeline (Classical): Jenkins or GitLab orchestrates code, build, and deployment tasks.
- QEE Interface: A middleware layer (e.g., Qiskit Runtime API) routes tasks to a quantum processor or simulator.
- Quantum Processor/Simulator: Executes quantum algorithms, connected via cloud (e.g., IBM Quantum, AWS Braket).
- Security Monitoring: Tools like Prometheus integrate quantum-enhanced anomaly detection.
[ DevSecOps Pipeline ] --> [ QEE API Gateway ] --> [ Job Orchestrator ]
↓
[ Security Module | IAM | PQC Firewall ]
↓
[ Quantum Backend Connector ] --> [ QPU or Simulator ]
↓
[ Logs / Observability Layer ]
Integration Points with CI/CD or Cloud Tools
- Jenkins/GitLab: Plugins or scripts to call QEE APIs for tasks like secure key generation.
- AWS Braket/Google Cloud Quantum: Cloud-based quantum services for scalable QEE access.
- Kubernetes: Orchestrates hybrid quantum-classical workloads in containerized environments.
| Tool | Integration |
|---|---|
| GitHub Actions | QEE job runner via GitHub Action. |
| GitLab CI | Pipeline stage for quantum circuit testing. |
| Jenkins | Quantum jobs as build steps. |
| AWS Braket | Native support via SDKs and QEE plugins. |
| Azure Quantum | QEE as a managed job resource. |
Installation & Getting Started
Basic Setup or Prerequisites
- Hardware/Cloud Access: Access to a quantum computer or simulator (e.g., IBM Quantum, AWS Braket).
- Software: Python 3.8+, Qiskit (or equivalent quantum SDK), and a CI/CD tool (e.g., Jenkins).
- Dependencies: Quantum-safe libraries like
liboqsfor cryptographic operations. - Environment: A secure cloud or on-premises environment with network access to quantum services.
Hands-on: Step-by-Step Beginner-Friendly Setup Guide
- Install Qiskit:
pip install qiskit- Set Up IBM Quantum Account:
- Sign up at quantum-computing.ibm.com.
- Obtain an API token and save it in ~/.qiskit/qiskitrc.
3. Configure CI/CD Pipeline:
- Install Jenkins and a Qiskit plugin (hypothetical, or use a custom script).
- Example Jenkins pipeline script:
pipeline {
agent any
stages {
stage('Quantum Security Check') {
steps {
sh 'python3 quantum_security_check.py'
}
}
}
}4. Write a Quantum Security Check:
- Example Python script using Qiskit for a quantum random number generator:
from qiskit import QuantumCircuit, Aer, execute
circuit = QuantumCircuit(4, 4)
circuit.h(range(4)) # Apply Hadamard gate for randomness
circuit.measure(range(4), range(4))
simulator = Aer.get_backend('qasm_simulator')
result = execute(circuit, simulator, shots=1).result()
print(result.get_counts())5. Integrate with CI/CD:
- Add the script to your repository and trigger it in the build stage.
6. Test and Verify:
- Run the pipeline and check for quantum-generated outputs in the logs.
Real-World Use Cases
1. Secure Code Signing in CI/CD
- Scenario: A financial institution uses QEE to generate quantum-safe cryptographic keys for signing code artifacts in a Jenkins pipeline, ensuring tamper-proof deployments.
- Industry: Finance, where regulatory compliance (e.g., PCI-DSS) demands strong security.
2. Vulnerability Scanning Optimization
- Scenario: A cybersecurity firm employs QEE to optimize static application security testing (SAST) using quantum algorithms to analyze complex codebases faster.
- Industry: Cybersecurity, where speed and accuracy are critical.
3. Quantum-Enhanced Anomaly Detection
- Scenario: A cloud provider integrates QEE with Prometheus to detect anomalies in production workloads using quantum machine learning, reducing false positives.
- Industry: Cloud Computing, for scalable monitoring.
4. Post-Quantum Cryptography Compliance
- Scenario: A government contractor uses QEE to implement NIST post-quantum cryptographic algorithms in their DevSecOps pipeline to meet federal standards.
- Industry: Public Sector, where compliance is mandatory.
Benefits & Limitations
Key Advantages
- Enhanced Security: Quantum-safe cryptography protects against future quantum attacks.
- Performance Optimization: Quantum algorithms accelerate tasks like optimization and pattern recognition.
- Scalability: Cloud-based QEE services (e.g., AWS Braket) scale with demand.
- Future-Proofing: Prepares pipelines for quantum computing advancements.
Common Challenges or Limitations
- Hardware Constraints: Limited access to quantum computers; simulators are slower.
- Complexity: Ste witch to a quantum-safe algorithm or integrating QEE with existing DevSecOps tools.
- Cost: Quantum cloud services can be expensive for smaller organizations.
- Maturity: Quantum computing is still nascent, with limited real-world deployments.
| Limitation | Description |
|---|---|
| Hardware Access | Limited public access to QPUs; most require wait times or simulators. |
| Steep Learning Curve | Quantum programming requires new skills. |
| Cost | Quantum compute time is expensive; simulations can be slow. |
| Tooling Gaps | Fewer mature tools than classical cloud-native environments. |
Best Practices & Recommendations
Security Tips
- Use quantum-safe cryptographic libraries (e.g., OpenQuantumSafe) for all sensitive operations.
- Implement least privilege principles in QEE access controls.
- Regularly update quantum SDKs to patch vulnerabilities.
Performance
- Use quantum simulators for development and testing to reduce costs.
- Optimize quantum circuits to minimize qubit usage and execution time.
Maintenance
- Monitor QEE performance with tools like Prometheus for latency and error rates.
- Automate quantum task orchestration using CI/CD plugins or scripts.
Compliance Alignment
- Align with NIST post-quantum cryptography standards for regulatory compliance.
- Document quantum operations for auditability in regulated industries.
Automation Ideas
- Automate quantum key generation in CI/CD pipelines using scripts like the one above.
- Integrate QEE with GitOps for version-controlled quantum configurations.
Comparison with Alternatives
| Feature | Quantum Execution Environment | Classical Containers (e.g., Docker) | Serverless (e.g., AWS Lambda) |
|------------------------|------------------------------|-------------------------------------|-------------------------------|
| Security | Quantum-safe cryptography | Standard encryption | Standard encryption |
| Performance | High for specific tasks | High for general tasks | High for event-driven tasks |
| Scalability | Cloud-based, limited by hardware | Highly scalable | Highly scalable |
| Complexity | High (quantum expertise needed) | Moderate | Low |
| Use Case | Cryptography, optimization | General-purpose apps | Event-driven apps |When to Choose QEE
- Choose QEE for workloads requiring quantum-safe cryptography or optimization (e.g., financial, cybersecurity applications).
- Opt for classical containers or serverless for general-purpose, cost-sensitive, or simpler applications.
Conclusion
Final Thoughts
The Quantum Execution Environment offers a transformative approach to DevSecOps, enabling organizations to leverage quantum computing for enhanced security and performance. While still in its early stages, QEE has significant potential for future-proofing pipelines against quantum threats and optimizing complex tasks.
Future Trends
- Quantum Hardware Advancements: Increased qubit counts and error correction will make QEE more practical.
- Hybrid Pipelines: Greater integration of quantum and classical systems in CI/CD.
- Regulatory Push: Adoption of quantum-safe standards by NIST and other bodies.
Next Steps
- Explore Qiskit tutorials at quantum-computing.ibm.com.
- Join communities like the Qiskit Slack or IBM Quantum Network.
- Experiment with quantum simulators to prototype QEE integration.
Links to Official Docs and Communities
- Qiskit Documentation: qiskit.org/documentation
- IBM Quantum: quantum-computing.ibm.com
- OpenQuantumSafe: openquantumsafe.org
- AWS Braket: aws.amazon.com/braket